
Browse The Best Cyber Security Store For Your Needs
Explore our curated selection of the best cyber security software. Compare, choose, and protect what matters most.
Welcome to Barricadem, your trusted cyber security store for top-rated tools to protect your devices, data, and identity. Whether you’re an individual, a freelancer, or a business, we’ve got the solutions you need to stay secure.
Why Choose Barricadem?
-
Consumer First
Our number one goal is to allow our customers straightforward insights in cyber security products. We review each product to ensure we are providing the best cybersecurity software for you.
-
Data Secured
Your data is protected and secured through Barricadem. We follow strict guidelines and laws to protect your data.
-
Always Evolving
We stay up-to-date with the latest threats and solutions, continuously expanding our cyber security store to offer you the best options available. We sometimes provide lesser known brands (hidden gems) to help you save money.
Find The Right Products For You And Your Family

Quick Facts
1. In 2024, the average cost of a data breach was $4.88 million, which was a record high (according to IBM).
2. It typically takes 194 days to find a breach (according to IBM).
3. Only an estimated 0.05% of cybercrime entities are likely to be found and prosecuted in the United States (according to the W.E.F.).
4. 64% of Americans have never looked to see if they were impacted by a breach (according to Varonis).
5. In the event of a data breach, 56% of Americans are unsure on what to do (according to Varonis).
Everyone Is At Risk
Many people think they’re not a target for cyberattacks because they’re not rich or famous, but that’s not true. Hackers often go after everyday people because they’re less likely to have strong security. Your personal information, like passwords, bank details, or even your identity, is valuable to them. Thinking you’re safe just because you’re “not important” can leave you vulnerable. Staying protected is smart for everyone, no matter who you are. This is why we provide the best cybersecurity software-to eliminate that risk.
Learn More About Cyber Security
Learn more about cyber security and how to protect yourself by reading our published articles.
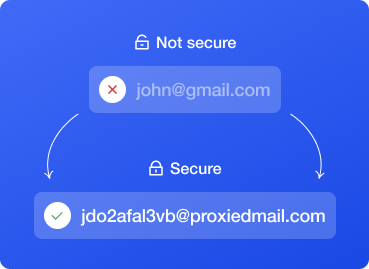
ProxiedMail
Proxies For Email Protection | Exclusive Annual Discount
Share

Blog posts
View all-

15-Step Security Compliance Checklist for 2025
In today’s digital world, staying compliant with security regulations is critical for businesses of all sizes. As cyber threats grow more sophisticated and regulations tighten, organizations must proactively safeguard their...
15-Step Security Compliance Checklist for 2025
In today’s digital world, staying compliant with security regulations is critical for businesses of all sizes. As cyber threats grow more sophisticated and regulations tighten, organizations must proactively safeguard their...
-

The Ultimate Guide to Email Security Software F...
In today’s digital age, remote work has become the norm for businesses worldwide. While this shift offers flexibility and productivity benefits, it also introduces unique cybersecurity challenges—especially when it comes...
The Ultimate Guide to Email Security Software F...
In today’s digital age, remote work has become the norm for businesses worldwide. While this shift offers flexibility and productivity benefits, it also introduces unique cybersecurity challenges—especially when it comes...
-

The Best Office 365 Security Checklist
Office 365 is a powerful tool for businesses, but without proper security measures, your data could be at risk. Whether you’re a small business or a large enterprise, securing your...
The Best Office 365 Security Checklist
Office 365 is a powerful tool for businesses, but without proper security measures, your data could be at risk. Whether you’re a small business or a large enterprise, securing your...


